Network servers, the unsung heroes of the digital age, form the backbone of modern networks, quietly orchestrating the flow of information and services that power our interconnected world. Imagine a bustling city where data packets are the citizens, and servers are the traffic controllers, ensuring smooth and efficient communication between every corner. From the websites we browse to the emails we send, network servers are the silent engines driving the digital landscape.
These powerful machines act as central hubs, storing, processing, and distributing data to numerous clients. Whether it’s a website hosting millions of users or a small office network sharing files, network servers play a vital role in enabling communication and access to critical resources.
What is a Network Server?
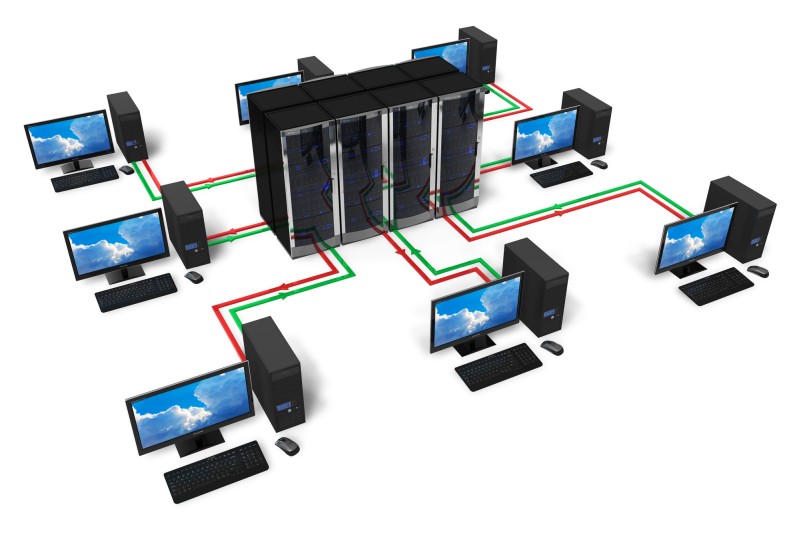
A network server is a powerful computer that acts as a central hub for a network, providing resources and services to other connected devices, like computers, laptops, smartphones, and printers.
Think of it as the central brain of a network, managing everything from file storage and sharing to internet access and security.
Types of Network Servers
Network servers come in various forms, each designed for specific tasks. Here are some common examples:
- File Servers: These servers store and manage files, allowing users to access and share data across the network. They are essential for businesses that need to collaborate on documents, store large datasets, or provide centralized file storage.
- Web Servers: These servers host websites and web applications, making them accessible to users over the internet. They process requests from web browsers, deliver web pages, and handle user interactions.
- Mail Servers: These servers handle email communication, receiving, sending, and storing emails for users on the network. They ensure emails are delivered securely and efficiently.
- Print Servers: These servers manage printing tasks, allowing users to share printers across the network. They handle print jobs, manage queues, and provide centralized control over printing resources.
- Database Servers: These servers store and manage large amounts of data, making it accessible to applications and users. They are essential for businesses that need to track customer information, manage inventory, or analyze large datasets.
- Game Servers: These servers host online games, allowing players to connect and interact with each other in virtual environments. They manage game sessions, handle player data, and ensure smooth gameplay.
Server Architecture and Components
A server is a complex system composed of various hardware and software components working together to provide services to clients. Understanding the architecture and components of a server is crucial for effective management and troubleshooting.
Hardware Components, Network server
The hardware components of a server form the physical foundation upon which the server operates. These components include:
- Processor (CPU): The central processing unit (CPU) is the brain of the server, responsible for executing instructions and processing data. A server’s CPU needs to be powerful enough to handle the demands of the applications and users it serves.
- Memory (RAM): Random access memory (RAM) provides temporary storage for data that the CPU is actively using. Servers typically require large amounts of RAM to handle multiple concurrent requests and applications.
- Storage: Servers utilize various storage devices to store data persistently, including hard disk drives (HDDs), solid-state drives (SSDs), and network-attached storage (NAS) devices. The type of storage used depends on the specific needs of the server, such as speed, capacity, and reliability.
- Network Interface Card (NIC): The network interface card (NIC) enables the server to connect to a network and communicate with other devices. Servers often have multiple NICs to support high-speed connections and redundancy.
- Power Supply: The power supply converts AC power to DC power, providing electricity to the server’s components. Servers may have multiple power supplies for redundancy and reliability.
- Chassis: The chassis provides a physical enclosure for the server’s components, protecting them from dust, moisture, and other environmental hazards.
Operating System
The operating system (OS) is a software program that manages the server’s hardware resources and provides a platform for applications to run. It acts as an intermediary between the hardware and the applications, handling tasks such as:
- Resource Management: The OS manages the server’s CPU, memory, storage, and network resources, allocating them efficiently to different applications and processes.
- Process Management: The OS creates, schedules, and manages processes, ensuring that multiple applications can run concurrently without interfering with each other.
- File System Management: The OS organizes and manages files and directories on the server’s storage devices, providing a hierarchical structure for data storage and retrieval.
- Security: The OS provides security features to protect the server from unauthorized access and malicious attacks. It enforces access controls, manages user accounts, and monitors system activity for suspicious behavior.
- Networking: The OS manages the server’s network connections, enabling communication with other devices on the network. It handles routing, addressing, and data transmission.
Physical vs. Virtual Servers
Servers can be classified as physical or virtual, depending on their underlying hardware infrastructure.
- Physical Servers: A physical server is a standalone computer system with its own dedicated hardware components. Each physical server runs a single operating system and can host multiple applications. Physical servers offer high performance and control but can be expensive to purchase and maintain.
- Virtual Servers: A virtual server is a software-based instance of a server that runs on top of a physical server. Virtualization software creates multiple virtual machines (VMs) on a single physical server, each with its own operating system and resources. Virtual servers are more cost-effective and flexible than physical servers, allowing for greater resource utilization and easier scalability.
Server Roles and Responsibilities
Servers play a crucial role in modern networks, each specializing in specific tasks to ensure smooth operation and efficient resource management. Understanding these roles is essential for comprehending how networks function and how servers interact to deliver services.
Common Server Roles
Servers are categorized based on their primary functions. Here are some of the most common server roles:
- Web Server: A web server is responsible for hosting websites and delivering web pages to users. It receives requests from clients (browsers) and sends back the requested content, including HTML, CSS, JavaScript, images, and videos. Popular web server software includes Apache, Nginx, and Microsoft IIS.
- File Server: A file server acts as a centralized storage location for files and data. It allows users to access, share, and manage files from different locations within a network. File servers often use protocols like SMB/CIFS (Windows) or NFS (Unix/Linux) to enable file sharing.
- Mail Server: A mail server handles the sending and receiving of emails within a network or organization. It receives emails from senders, stores them, and delivers them to recipients. Popular mail server software includes Postfix, Sendmail, and Microsoft Exchange Server.
- Database Server: A database server manages and stores large amounts of data in an organized and structured way. It provides access to data for applications and users, ensuring data integrity and consistency. Popular database server software includes MySQL, PostgreSQL, and Oracle Database.
- Print Server: A print server acts as an intermediary between printers and network users. It manages print jobs, queues them, and sends them to the appropriate printer. This allows multiple users to share printers without needing to connect them directly to each computer.
- Application Server: An application server runs and manages applications, providing a platform for them to execute and interact with other components of the network. It often handles tasks like user authentication, data access, and application logic.
Server Role Interactions
Different server roles often work together to provide comprehensive network services. For example:
- Web Server and Database Server: A web server might rely on a database server to store and retrieve information about users, products, or other dynamic content. The web server sends requests to the database server, which processes the data and returns it to the web server for display to the user.
- Mail Server and File Server: A mail server might store attachments on a file server, allowing users to access them from their email accounts. The mail server interacts with the file server to retrieve and deliver attachments.
- Application Server and Other Servers: An application server often interacts with other servers to access data, perform calculations, or manage resources. It might use a database server for data storage, a file server for storing application files, or a web server for displaying user interfaces.
Network Server Security
Network server security is paramount for any organization, as it safeguards sensitive data and ensures the smooth operation of critical business processes. Protecting servers from unauthorized access, data breaches, and malware is essential for maintaining data integrity, business continuity, and user privacy.
Key Security Vulnerabilities
Network servers are susceptible to a range of security vulnerabilities that can compromise their integrity and expose sensitive data. Understanding these vulnerabilities is crucial for implementing effective security measures.
- Operating System and Software Vulnerabilities: Outdated operating systems and software applications often contain known security flaws that attackers can exploit. These vulnerabilities can provide access to sensitive data or allow attackers to take control of the server.
- Weak Passwords: Using simple or easily guessed passwords can make servers vulnerable to brute-force attacks, where attackers try numerous password combinations until they find the correct one.
- Misconfigured Security Settings: Improperly configured security settings, such as weak firewall rules or permissive access controls, can create security loopholes that attackers can exploit.
- Network Security Weaknesses: Inadequate network security measures, such as lack of encryption or insufficient network segmentation, can expose servers to external threats.
- Social Engineering: Attackers can use social engineering tactics to trick users into providing access to sensitive information or granting them unauthorized access to the server.
- Physical Security Risks: Servers located in physically insecure environments can be vulnerable to theft, damage, or unauthorized access.
Best Practices for Securing Network Servers
Implementing best practices for securing network servers is essential to mitigate security risks and protect sensitive data.
- Regularly Patch and Update Systems: Regularly patching and updating operating systems and software applications is crucial to address known vulnerabilities and protect servers from exploitation.
- Use Strong Passwords and Multi-Factor Authentication: Enforce strong passwords and multi-factor authentication to prevent unauthorized access to servers.
- Implement Strong Access Controls: Configure strict access controls to limit access to sensitive data and resources based on user roles and permissions.
- Regularly Audit Security Settings: Regularly audit security settings to ensure they are up-to-date and effective in preventing unauthorized access.
- Use Secure Network Protocols: Implement secure network protocols, such as HTTPS and SSH, to encrypt data transmitted over the network.
- Enable Network Segmentation: Segment the network to isolate critical servers and reduce the impact of security breaches.
- Implement Data Loss Prevention (DLP) Solutions: Use DLP solutions to prevent sensitive data from leaving the network unauthorized.
- Train Users on Security Best Practices: Train users on security best practices, such as password management, phishing awareness, and reporting suspicious activity.
- Secure Physical Environments: Ensure physical security measures are in place to protect servers from theft, damage, and unauthorized access.
Role of Firewalls and Intrusion Detection Systems
Firewalls and intrusion detection systems play crucial roles in securing network servers by preventing unauthorized access and detecting malicious activity.
- Firewalls: Firewalls act as a barrier between the server and the outside world, blocking unauthorized access and filtering incoming and outgoing network traffic. They enforce security policies by allowing only authorized traffic to pass through.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity and alert administrators to potential security threats. They analyze network traffic patterns and identify anomalies that may indicate an attack.
Server Management and Administration
Server management is the process of overseeing and maintaining the operation of a server, ensuring its smooth performance, security, and availability. This involves a wide range of tasks, from routine monitoring to complex troubleshooting and optimization. Effective server management is crucial for any organization that relies on servers for its operations, as it directly impacts the reliability and performance of critical systems and applications.
Server Management Tools and Techniques
A variety of tools and techniques are employed to manage servers efficiently. These tools provide a centralized platform for monitoring server health, performance, and security, simplifying administrative tasks and streamlining operations.
- Remote Access Tools: Tools like SSH (Secure Shell) and RDP (Remote Desktop Protocol) enable administrators to connect to and manage servers remotely, regardless of their physical location. This is essential for troubleshooting issues, installing software, and performing routine maintenance tasks.
- Command-Line Interfaces (CLIs): CLIs offer a powerful way to interact with servers, allowing administrators to execute commands and scripts for various tasks. Popular CLIs include Bash, PowerShell, and Zsh.
- Graphical User Interfaces (GUIs): GUIs provide a user-friendly interface for managing servers, simplifying tasks like configuring services, managing users, and monitoring system resources. Examples include Windows Server Manager and Webmin.
- Server Management Software: Dedicated server management software provides a comprehensive suite of tools for managing servers, including monitoring, automation, and security. Popular options include Ansible, Puppet, Chef, and SaltStack.
Importance of Regular Server Maintenance and Updates
Regular server maintenance and updates are essential for ensuring optimal performance, security, and stability. Neglecting these tasks can lead to various problems, including performance degradation, security vulnerabilities, and system instability.
- Performance Optimization: Routine maintenance tasks like disk cleanup, log file management, and resource optimization can significantly improve server performance, reducing bottlenecks and enhancing application responsiveness.
- Security Patching: Regularly applying security updates and patches is crucial for mitigating vulnerabilities and protecting against malicious attacks. Software vendors release updates to address security flaws, and failing to apply them can expose servers to significant risks.
- System Stability: Regular maintenance ensures that the server operating system and applications are up-to-date, reducing the likelihood of crashes and system instability. This minimizes downtime and ensures uninterrupted service availability.
Server Monitoring and Troubleshooting
Effective server monitoring and troubleshooting are crucial for identifying and resolving issues before they impact system performance or availability. Monitoring tools provide real-time insights into server health, performance, and resource utilization, allowing administrators to proactively identify and address potential problems.
- System Monitoring Tools: Tools like Nagios, Zabbix, and Prometheus provide comprehensive monitoring capabilities, tracking server metrics such as CPU usage, memory utilization, disk space, and network traffic. These tools can trigger alerts when predefined thresholds are exceeded, allowing administrators to intervene promptly.
- Log Analysis: Analyzing server logs is essential for identifying and diagnosing problems. Logs contain detailed information about system events, errors, and warnings, providing valuable clues for troubleshooting. Tools like Splunk and Graylog can simplify log analysis and provide insights into system behavior.
- Performance Profiling: Profiling tools help identify performance bottlenecks and optimize server resource utilization. Tools like Valgrind and gprof analyze application code to pinpoint areas where performance can be improved.
Server Deployment and Configuration
Deploying and configuring a network server is a crucial step in establishing a functional and secure network infrastructure. This process involves several stages, each contributing to the overall performance and reliability of the server.
Steps Involved in Deploying a Network Server
Deploying a network server typically involves a series of steps, each contributing to the server’s functionality and security.
- Planning and Requirements Gathering: This initial phase involves defining the server’s purpose, the applications it will host, the anticipated workload, and the required resources, such as storage, memory, and network bandwidth. It also involves considering security requirements, including access control, data encryption, and firewall configuration.
- Hardware Selection: Based on the requirements gathered, the appropriate hardware components are selected. This includes choosing the server chassis, processor, memory, storage, and network interfaces. The choice of hardware depends on the server’s intended role, workload, and budget.
- Operating System Installation: Once the hardware is assembled, the chosen operating system is installed. This could be a server-specific distribution of Linux, such as Red Hat Enterprise Linux (RHEL) or CentOS, or a server edition of Windows, such as Windows Server. The operating system provides the foundation for running applications and managing the server.
- Network Configuration: Configuring the server’s network settings is essential for connectivity. This includes assigning a static IP address, configuring DNS settings, and configuring the firewall. Secure network configuration is crucial for protecting the server from unauthorized access.
- Application Installation and Configuration: Depending on the server’s role, various applications are installed and configured. This might include web servers (Apache, Nginx), database servers (MySQL, PostgreSQL), email servers (Postfix, Sendmail), or other specialized applications. The configuration of these applications is crucial for their proper operation and security.
- Security Configuration: Implementing security measures is paramount for protecting the server and its data. This involves configuring firewalls, setting up user accounts with appropriate privileges, implementing access control lists, and enabling security updates for the operating system and applications.
- Testing and Optimization: After deployment, the server is thoroughly tested to ensure it meets the performance and reliability requirements. This involves running load tests, stress tests, and security audits. Based on the test results, the server configuration can be further optimized for better performance and resource utilization.
- Monitoring and Maintenance: Ongoing monitoring and maintenance are essential for ensuring the server’s stability and uptime. This involves monitoring server performance metrics, such as CPU utilization, memory usage, and disk space, and implementing regular maintenance tasks, such as software updates and security patches.
Common Server Configuration Options
Server configuration options allow administrators to customize the server’s behavior and optimize its performance.
- Network Configuration: This includes setting up the server’s IP address, subnet mask, default gateway, and DNS settings. It also involves configuring the firewall, which acts as a barrier against unauthorized access to the server.
- Storage Configuration: This involves defining the file systems, disk quotas, and storage access permissions. Depending on the server’s role, different storage configurations might be required, such as RAID configurations for redundancy and performance enhancement.
- Security Configuration: This involves setting up user accounts, defining access control lists, and configuring security settings for the operating system and applications. Security configurations aim to protect the server from unauthorized access, malware, and data breaches.
- Performance Tuning: This involves adjusting system parameters and resource allocation to optimize the server’s performance for specific workloads. This might include tweaking the CPU scheduling algorithm, adjusting memory settings, or optimizing the network configuration.
- Logging and Monitoring: Setting up logging and monitoring tools allows administrators to track server activity, identify potential problems, and diagnose issues. This includes configuring system logs, performance monitoring tools, and event logs.
Virtualization for Server Deployment
Virtualization offers a powerful approach to server deployment, enabling multiple virtual servers (VMs) to run on a single physical server.
- Benefits of Virtualization:
- Resource Optimization: Virtualization allows multiple servers to share the resources of a single physical server, leading to better resource utilization and reduced hardware costs.
- Improved Flexibility: Virtualization enables the creation of virtual servers with different operating systems and configurations, providing flexibility and agility in server deployment and management.
- Simplified Management: Virtualization platforms offer centralized management tools, simplifying the administration of multiple virtual servers. This includes tasks like provisioning, monitoring, and patching.
- Disaster Recovery: Virtualization simplifies disaster recovery by allowing quick restoration of virtual servers from backups. This can be done on a different physical server, minimizing downtime in case of hardware failures.
- Popular Virtualization Platforms:
- VMware vSphere: A comprehensive virtualization platform offering a wide range of features, including live migration, high availability, and advanced networking capabilities.
- Microsoft Hyper-V: A built-in virtualization solution in Windows Server, providing a cost-effective option for server virtualization.
- Oracle VirtualBox: A free and open-source virtualization platform suitable for personal and small business use, allowing users to run multiple operating systems on a single computer.
- KVM (Kernel-based Virtual Machine): A Linux-based virtualization solution, offering high performance and integration with Linux operating systems.
Network Server Technologies
Network servers rely on a set of protocols and technologies to communicate and exchange data effectively. These technologies underpin the functionality of servers, enabling them to connect to other devices, share resources, and provide essential services.
Common Network Protocols
Network protocols define the rules and formats for data exchange between devices. Servers utilize a range of protocols, with some of the most common ones being:
- TCP/IP (Transmission Control Protocol/Internet Protocol): This foundational protocol suite forms the backbone of the internet and many private networks. TCP provides reliable, ordered delivery of data, while IP handles the addressing and routing of packets.
- HTTP (Hypertext Transfer Protocol): This protocol is essential for web servers, enabling the transfer of web pages, images, and other content between web servers and web browsers.
- FTP (File Transfer Protocol): FTP allows for the transfer of files between computers. It’s often used to upload and download files to and from servers.
- SMTP (Simple Mail Transfer Protocol): SMTP is the standard protocol for sending emails. Mail servers use SMTP to send and receive emails.
- DNS (Domain Name System): DNS is a hierarchical and distributed naming system that translates human-readable domain names into numerical IP addresses. This allows computers to communicate with each other using easy-to-remember names rather than complex IP addresses.
DNS and Server Communication
DNS plays a critical role in server communication by acting as a directory service. When a user enters a website address, such as “google.com,” the DNS server resolves this domain name into the corresponding IP address of the Google web server. This allows the user’s computer to establish a connection with the correct server and access the website. DNS ensures that servers can be located and accessed efficiently.
Cloud Computing’s Impact on Network Servers
Cloud computing has revolutionized the way network servers are deployed and managed. Instead of relying on physical servers located in a data center, cloud computing allows users to access server resources over the internet. This offers several benefits, including:
- Scalability: Cloud servers can be easily scaled up or down based on demand, allowing organizations to adjust their resources dynamically.
- Cost-effectiveness: Cloud computing often provides a pay-as-you-go model, reducing upfront infrastructure costs and allowing organizations to only pay for the resources they use.
- Accessibility: Cloud servers can be accessed from anywhere with an internet connection, improving remote access and collaboration.
- Flexibility: Cloud computing offers a wide range of services, such as storage, databases, and application hosting, providing flexibility in server deployments.
Cloud computing has significantly shifted the landscape of network servers, offering new opportunities for organizations to leverage server resources efficiently and effectively.
Server Applications and Services
Servers are the backbone of modern computing, providing a wide range of applications and services that power our digital world. These applications enable various functionalities, from accessing websites to managing databases and facilitating communication.
Server applications are software programs that run on servers, providing specific services to clients. They are designed to handle requests from multiple clients simultaneously, ensuring efficient and reliable service delivery.
Types of Server Applications
Server applications are categorized based on their specific functions and the services they provide. Here are some of the most common types:
- Web Servers: These servers handle requests for web pages and other web-based content. Popular examples include Apache, Nginx, and Microsoft IIS.
- Database Servers: These servers store and manage large amounts of data, providing efficient access and retrieval. Examples include MySQL, PostgreSQL, and Oracle Database.
- Mail Servers: These servers handle email transmission and storage, enabling communication between users. Common examples include Postfix, Sendmail, and Microsoft Exchange Server.
- File Servers: These servers provide centralized storage and access to files, allowing users to share and manage documents and other data. Examples include Samba and Windows Server.
- Application Servers: These servers provide a platform for running complex applications, handling requests and managing resources. Popular examples include JBoss, WebSphere, and Tomcat.
Client-Server Architecture
Client-server architecture is a common network model where clients request services from servers. Clients are typically devices like computers, smartphones, or tablets, while servers provide resources and services. This model allows for centralized management, scalability, and security.
- Clients: Clients initiate requests to access resources or services provided by the server.
- Servers: Servers process requests from clients, providing the requested services or resources. They are responsible for managing data, applications, and network resources.
- Communication: Clients and servers communicate using network protocols, such as TCP/IP, to exchange information.
Interaction Between Server Applications and Clients
Server applications interact with clients through a well-defined communication process. Clients send requests to the server, which then processes the request and sends a response back to the client.
- Request: Clients send requests to the server using specific protocols, such as HTTP for web servers or SMTP for mail servers.
- Processing: The server receives the request and processes it according to its functionality. This might involve accessing data, executing code, or performing other operations.
- Response: The server sends a response back to the client, indicating the outcome of the request. This response might contain data, an error message, or confirmation of the request’s completion.
End of Discussion
As technology continues to evolve, network servers are becoming increasingly sophisticated, adapting to the ever-growing demands of the digital age. From cloud computing to edge computing, new paradigms are emerging, transforming the way we think about server infrastructure. Understanding the intricacies of network servers is crucial for anyone navigating the complexities of the digital world, empowering individuals and organizations to harness the full potential of these powerful tools.
A network server acts as a central hub, providing resources and services to connected devices. Imagine it as a master craftsman, skillfully managing the flow of information, much like someone meticulously crafting intricate bows, making bows with precision and artistry.
The server ensures smooth communication and efficient data exchange, just as the bowmaker ensures each bow is perfectly balanced and ready to perform.




