NTP Server, the timekeeper of the digital world, plays a crucial role in ensuring that devices across a network operate in perfect harmony. Imagine a network where clocks are misaligned – transactions could be delayed, security could be compromised, and even simple tasks could become a chaotic mess. NTP servers act as the central authority, broadcasting precise time signals to all connected devices, guaranteeing seamless communication and reliable operations.
From the intricate workings of financial institutions to the smooth operation of online gaming platforms, accurate timekeeping is essential. NTP servers provide this vital service, ensuring that time is not just a number, but a critical element in the efficiency and security of modern networks.
NTP Server Functionality
An NTP server is a crucial component in maintaining accurate time synchronization across a network. It plays a vital role in ensuring that devices within a network operate in harmony, with consistent timekeeping across all systems.
NTP servers work by using a specialized protocol to synchronize time with other NTP servers and clients. The process involves a series of communication exchanges between the server and its peers, resulting in the dissemination of accurate time information throughout the network.
An NTP server is crucial for maintaining accurate time synchronization across your network. If you’re considering a move to cloud server hosting , be sure to factor in the need for a reliable NTP server. It’s essential to ensure your cloud infrastructure is properly synchronized for optimal performance and security.
NTP Protocols and Variations
The Network Time Protocol (NTP) is a communication protocol that enables time synchronization across a network. Different versions of the NTP protocol have evolved over time, each with its own set of features and capabilities.
- NTPv1: The initial version of the NTP protocol, released in 1985. It provided basic time synchronization functionality but lacked some of the advanced features present in later versions.
- NTPv2: Introduced in 1989, NTPv2 incorporated significant improvements over its predecessor. It included enhancements such as improved security measures and a more robust time synchronization algorithm.
- NTPv3: Released in 1992, NTPv3 introduced further refinements to the protocol, including support for authentication, improved packet formats, and enhanced time synchronization accuracy.
- NTPv4: The latest version of the NTP protocol, released in 2010. It provides enhanced security features, improved performance, and support for IPv6. It also includes several new features, such as support for symmetric key cryptography and a more efficient time synchronization algorithm.
Key Components of an NTP Server Configuration
Configuring an NTP server involves defining several key parameters that determine how the server operates. These components play a crucial role in ensuring the server’s performance and reliability.
- Time Source: This parameter specifies the primary time source that the NTP server will use to synchronize its time. It can be a trusted external time source, such as an atomic clock or a GPS receiver, or another NTP server.
- Peer List: This list defines the other NTP servers that the server will communicate with to synchronize its time. The peer list should include a diverse set of servers, spread across different geographical locations and network providers, to minimize the impact of potential network outages or server failures.
- Authentication: This setting enables the server to verify the authenticity of time information received from other NTP servers. Authentication helps prevent malicious attacks and ensures that only trusted sources can contribute to the time synchronization process.
- Access Control: This feature allows administrators to restrict access to the NTP server, preventing unauthorized clients from synchronizing their time with the server. Access control helps ensure the server’s security and prevents potential misuse.
- Logging: Enabling logging allows administrators to monitor the server’s activity, including time synchronization events, communication with peers, and any errors or warnings. This information is valuable for troubleshooting and ensuring the server’s proper operation.
NTP Server Configuration
Configuring an NTP server involves setting up the server to synchronize time with other NTP servers or time sources. This ensures accurate timekeeping across your network, essential for applications relying on precise time synchronization.
Basic Configuration
The fundamental configuration of an NTP server involves defining its role, specifying the time sources it should use, and setting up security measures.
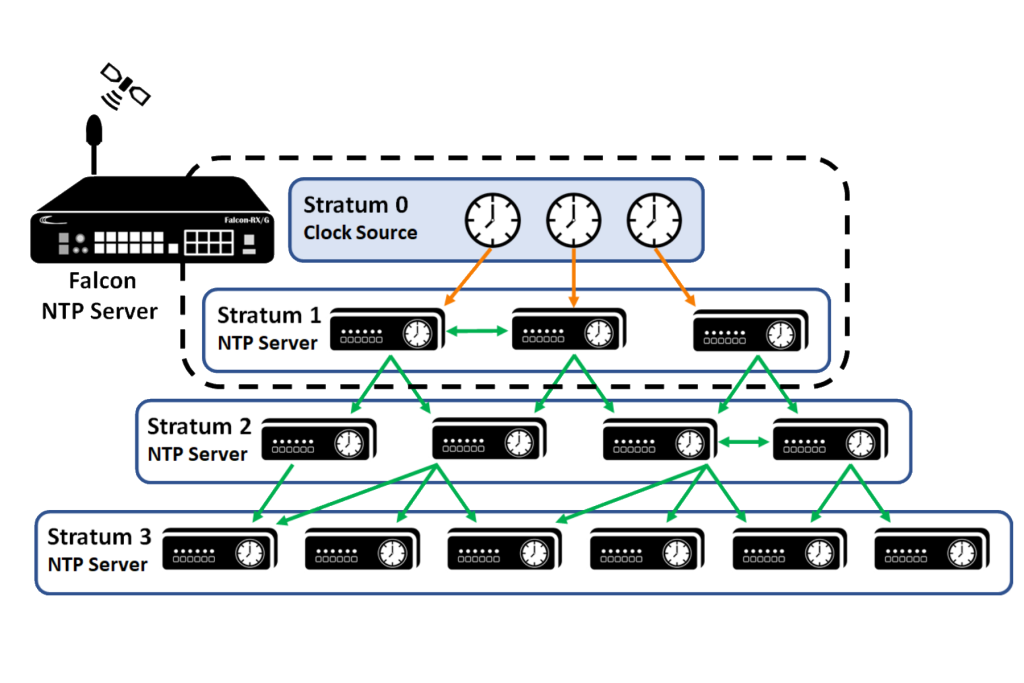
- NTP Server Role: The server can act as a primary time source, a secondary time source, or a client. A primary time source is typically a stratum 1 server directly connected to a time source like an atomic clock. Secondary servers synchronize with primary servers and act as time sources for clients. Clients receive time information from servers.
- Time Sources: The server needs to be configured with a list of time sources, known as peers. These peers can be other NTP servers or reference clocks.
- Security Measures: Security measures are crucial to prevent unauthorized access and manipulation of the NTP server. This includes using authentication protocols like symmetric key authentication (MD5 or SHA) and access control lists (ACLs) to restrict access.
Configuration Parameters
Several parameters influence the performance and behavior of an NTP server. Understanding these parameters is essential for optimizing the server for your specific needs.
- Stratum Level: This indicates the server’s position in the NTP hierarchy. Stratum 1 servers are directly connected to a time source, while stratum 2 servers synchronize with stratum 1 servers, and so on. The stratum level influences the accuracy and reliability of the time information provided by the server.
- Drift File: The drift file stores the server’s clock offset and other parameters used to adjust the clock.
- Poll Interval: This determines how frequently the server contacts its peers to synchronize its clock. A shorter poll interval leads to faster synchronization but increases network traffic.
- Broadcast and Multicast: These options enable the server to broadcast or multicast time information to clients on the network.
Security Configuration
Security is paramount for an NTP server, as it is a critical component of network infrastructure. Implementing security measures helps protect the server from unauthorized access and manipulation.
- Authentication: Use symmetric key authentication (MD5 or SHA) to verify the authenticity of time information received from peers. This ensures that only trusted sources can influence the server’s time.
- Access Control Lists (ACLs): Configure ACLs to restrict access to the NTP server. This allows only authorized clients to connect and receive time information.
- Firewall Rules: Implement firewall rules to block unauthorized access to the NTP server. This helps prevent malicious actors from exploiting vulnerabilities in the server.
- Security Patches: Regularly apply security patches to address vulnerabilities in the NTP server software. This ensures the server remains protected from known exploits.
NTP Server Security
NTP servers, crucial for time synchronization across networks, can be vulnerable to various security risks. These risks can impact the accuracy of timekeeping, network operations, and overall system security. Implementing robust security measures is essential to protect NTP servers and ensure their reliability.
Security Risks
NTP servers are susceptible to various security threats, including:
- Denial-of-Service (DoS) Attacks: Attackers can flood an NTP server with malicious requests, overwhelming its resources and making it unavailable to legitimate clients. These attacks can disrupt time synchronization and affect network operations.
- Spoofing: Malicious actors can spoof their IP addresses, pretending to be legitimate clients and sending incorrect time information to other devices. This can compromise the accuracy of timekeeping and potentially expose sensitive data.
- Man-in-the-Middle (MitM) Attacks: Attackers can intercept communication between NTP servers and clients, modifying or injecting false time information. This can lead to unauthorized access, data manipulation, and disruption of critical services.
- Configuration Vulnerabilities: Misconfigurations, such as weak authentication or insufficient access control, can create vulnerabilities that attackers can exploit to gain unauthorized access or manipulate the server.
- Software Vulnerabilities: Outdated or unpatched NTP server software can contain security vulnerabilities that attackers can exploit to gain control of the server or compromise the network.
Security Best Practices
Implementing the following best practices can help mitigate security risks associated with NTP servers:
- Use Strong Authentication: Implement strong authentication mechanisms, such as password-based authentication, public-key cryptography, or digital certificates, to prevent unauthorized access to the server.
- Restrict Access: Configure the server to only allow access from authorized clients and networks. Use access control lists (ACLs) to filter traffic and prevent unauthorized connections.
- Enable Security Features: Utilize built-in security features, such as packet filtering, intrusion detection systems (IDS), and firewalls, to detect and block malicious traffic.
- Keep Software Up-to-Date: Regularly update the NTP server software to address security vulnerabilities and ensure the latest security patches are applied.
- Monitor Server Activity: Monitor server logs for suspicious activity, such as unusual access patterns or unexpected errors. Implement alerts to notify administrators of potential security incidents.
- Use Secure Communication Protocols: Utilize secure communication protocols like Transport Layer Security (TLS) or Secure Shell (SSH) to encrypt data transmission between the server and clients, protecting sensitive information from eavesdropping.
Security Policy
A comprehensive security policy should be developed and implemented for NTP server deployment, addressing the following aspects:
- Authentication and Authorization: Define authentication methods, access control policies, and authorization levels for users and clients accessing the server.
- Network Security: Specify network segmentation, firewall rules, and access control measures to restrict access to the server and prevent unauthorized connections.
- Software Management: Establish procedures for software updates, patch management, and vulnerability assessment to ensure the server is kept secure and up-to-date.
- Security Monitoring: Define monitoring practices, logging policies, and incident response procedures to detect and respond to security threats promptly.
- Data Protection: Implement measures to protect sensitive data stored or processed by the server, such as encryption, access control, and data backup.
NTP Server Monitoring and Management
Keeping a close eye on your NTP server is essential for maintaining accurate time across your network. Regular monitoring helps you identify and address potential issues before they impact your systems.
Key Performance Indicators (KPIs)
Monitoring your NTP server involves tracking key performance indicators (KPIs) that reveal its health and performance. These metrics provide insights into how well the server is functioning and any potential problems.
- Response Time: This measures the time it takes for the NTP server to respond to requests from clients. A high response time indicates potential network congestion or server overload.
- Poll Interval: This is the frequency at which clients poll the NTP server for time updates. A long poll interval might indicate network issues or a high client load.
- Stratum Level: This indicates the server’s position in the NTP hierarchy. A lower stratum level (closer to the primary time source) signifies better accuracy. A sudden increase in the stratum level could signal a problem with the upstream time source.
- Peer Count: The number of peers the NTP server is synchronized with. A low peer count could suggest connectivity issues or a lack of redundancy.
- Dispersion: The maximum difference between the NTP server’s time and its peers. A high dispersion value could indicate a problem with the time source or a synchronization issue.
Management and Maintenance Plan
A comprehensive management and maintenance plan ensures your NTP server remains reliable and secure. This plan should include:
- Regular Monitoring: Implement a system to track the KPIs mentioned above, and establish thresholds to trigger alerts for potential issues.
- Backup and Recovery: Create regular backups of the NTP server’s configuration and data. Develop a recovery plan in case of data loss or server failure.
- Security Updates: Keep the NTP server’s software up to date with the latest security patches to protect against vulnerabilities.
- Log Analysis: Review the NTP server’s logs regularly to identify potential problems or security events.
- Performance Tuning: Optimize the NTP server’s configuration based on your network size and traffic to ensure efficient operation.
NTP Server Deployment Scenarios
NTP servers are essential components in modern IT infrastructure, ensuring accurate time synchronization across networks and devices. Understanding the various deployment scenarios and their associated challenges is crucial for successful implementation. This section delves into real-world examples of NTP server usage, explores considerations for different environments, and provides a case study showcasing the benefits of deploying an NTP server.
Real-World Deployment Scenarios
NTP servers are deployed in diverse environments to address specific time synchronization requirements. Here are some examples:
- Financial institutions rely on NTP servers for accurate timestamps in trading systems, ensuring compliance with regulatory requirements and preventing discrepancies in financial transactions.
- Data centers use NTP servers to synchronize clocks across servers, databases, and other critical infrastructure components, ensuring consistent data integrity and accurate logging.
- Telecommunication networks employ NTP servers to synchronize network devices, enabling seamless communication and accurate billing.
- Scientific research facilities utilize NTP servers for precise timekeeping in experiments and data analysis, ensuring accurate measurements and consistent results.
Challenges and Considerations for Different Environments
Deploying NTP servers in different environments presents unique challenges and considerations. Factors to consider include:
- Network topology: The network infrastructure, including the number of devices, bandwidth, and latency, can impact NTP server performance and accuracy.
- Security: Ensuring the security of the NTP server is crucial to prevent unauthorized access and manipulation of time data.
- Scalability: The ability to handle a large number of clients and maintain accurate time synchronization is essential for large-scale deployments.
- Reliability: High availability and fault tolerance are critical for ensuring continuous time synchronization, even in the event of failures.
Case Study: Benefits of NTP Server in a Large Enterprise Network
Consider a large enterprise network with hundreds of servers, workstations, and network devices. Without an NTP server, time synchronization across the network would be inconsistent, leading to various issues:
- Inaccurate logging: Timestamps in system logs would be unreliable, making it difficult to troubleshoot problems and track events.
- Data integrity issues: Databases and other applications relying on accurate timestamps could experience inconsistencies, leading to data corruption and loss.
- Performance degradation: Time discrepancies between devices could affect network performance, leading to delays and packet loss.
By deploying an NTP server, the enterprise can achieve:
- Accurate time synchronization across the entire network, ensuring consistent timestamps for all devices.
- Improved security by preventing unauthorized access and manipulation of time data.
- Enhanced performance by minimizing time discrepancies between devices, leading to faster network communication and reduced latency.
- Simplified management by providing a centralized point of control for time synchronization across the network.
NTP Server Tools and Resources
The realm of NTP server administration is enriched by a collection of powerful tools and resources. These tools provide administrators with the means to effectively configure, manage, and monitor NTP servers, ensuring accurate time synchronization across networks.
Popular NTP Server Software and Tools
Several NTP server software solutions are available, each with its strengths and features.
- NTPd: The Network Time Protocol daemon, NTPd, is the foundational NTP server software. It is a widely adopted, robust, and feature-rich solution that is included in most Linux distributions. NTPd offers a comprehensive set of features for configuring, managing, and monitoring NTP servers.
- Chrony: Chrony is a high-precision NTP client and server that focuses on accuracy and stability. It excels in environments where low latency and precise time synchronization are critical, such as financial institutions and scientific research. Chrony is known for its efficient resource usage and its ability to handle network fluctuations.
- OpenNTPD: OpenNTPD is a lightweight and efficient NTP server implementation. It is often preferred for its minimal resource footprint, making it suitable for embedded systems and resource-constrained environments. OpenNTPD provides essential NTP functionality, including time synchronization and peer management.
Useful Resources for Learning More About NTP Servers and Best Practices
The world of NTP servers is brimming with resources that can help you delve deeper into the intricacies of NTP configuration, troubleshooting, and best practices.
- NTP Pool Project: The NTP Pool Project is a collaborative effort that provides a network of publicly accessible NTP servers. It offers a reliable source of time synchronization for individuals and organizations. The project’s website provides valuable information on NTP configuration, server selection, and best practices.
- RFC 5905: RFC 5905, titled “Network Time Protocol (NTP) Version 4,” serves as the definitive specification for the NTP protocol. It Artikels the protocol’s design, operation, and security mechanisms, providing a comprehensive understanding of NTP.
- NTP Mailing List: The NTP mailing list is a vibrant online community where NTP users and developers exchange knowledge, share experiences, and discuss technical aspects of NTP. It offers a valuable platform for learning from experts and engaging in discussions on various NTP-related topics.
NTP Server Vendors and Their Offerings
Several vendors specialize in providing NTP server solutions, offering tailored features and support for various needs.
- Meinberg: Meinberg is a renowned vendor known for its high-precision time synchronization solutions, including NTP servers. Meinberg’s offerings cater to industries with strict time synchronization requirements, such as telecommunications, finance, and power grids.
- Galileo: Galileo provides a range of NTP server solutions, from hardware appliances to software-based implementations. Their offerings are designed to meet the specific needs of organizations across various sectors, ensuring accurate time synchronization and network stability.
- Time & Date: Time & Date is a leading provider of time synchronization services, including NTP servers. Their solutions are widely deployed in various industries, ensuring accurate timekeeping for critical applications and systems.
NTP Server Future Trends
The realm of time synchronization is constantly evolving, with NTP servers playing a pivotal role in maintaining accurate time across diverse networks. The future of NTP server technology holds exciting possibilities, driven by advancements in hardware, software, and network infrastructure.
Emerging Trends and Advancements
The future of NTP server technology is shaped by emerging trends and advancements that aim to enhance accuracy, reliability, and security.
- Improved Time Accuracy: Advancements in atomic clocks and timekeeping technologies will lead to even more precise time synchronization. This will be crucial for applications requiring ultra-low latency, such as high-frequency trading and scientific research.
- Enhanced Security: As cyber threats evolve, NTP servers will need to incorporate robust security measures to prevent attacks and ensure the integrity of time data. This includes implementing encryption protocols, authentication mechanisms, and access control policies.
- Cloud-Based NTP Services: The rise of cloud computing has paved the way for cloud-based NTP services. These services offer scalability, flexibility, and reduced management overhead, making them attractive for organizations of all sizes.
- Integration with Network Time Protocol (NTP)v4: NTPv4 introduces new features and enhancements, such as improved security, increased accuracy, and support for IPv6. Implementing NTPv4 will enhance the resilience and reliability of time synchronization systems.
Potential Future Applications and Use Cases
The role of NTP servers will expand beyond traditional time synchronization applications, encompassing new use cases driven by emerging technologies.
- Internet of Things (IoT): As the number of connected devices grows exponentially, NTP servers will play a critical role in synchronizing time across IoT networks. This will enable accurate data collection, analysis, and decision-making for various applications, such as smart cities and industrial automation.
- Blockchain Technology: Blockchain applications rely on precise timestamps to ensure the integrity and immutability of transactions. NTP servers will be crucial for providing accurate time synchronization in blockchain networks, enhancing security and trust.
- 5G Networks: The deployment of 5G networks will demand ultra-low latency and high-precision time synchronization for real-time applications, such as autonomous vehicles and virtual reality. NTP servers will be essential for meeting these requirements.
- Edge Computing: As computing power shifts to the edge, NTP servers will need to be deployed closer to edge devices to ensure accurate time synchronization. This will be crucial for applications requiring low latency and high availability, such as industrial control systems and real-time data processing.
Impact of New Technologies on NTP Server Implementation
New technologies are transforming the landscape of NTP server implementation, offering both challenges and opportunities.
- Artificial Intelligence (AI): AI can be used to automate NTP server management tasks, such as monitoring, configuration, and troubleshooting. This can improve efficiency and reduce the need for manual intervention.
- Software-Defined Networking (SDN): SDN enables centralized control and automation of network infrastructure, including NTP servers. This allows for dynamic configuration and optimization of time synchronization services based on network conditions and application requirements.
- Network Function Virtualization (NFV): NFV enables the virtualization of network functions, including NTP servers, on commodity hardware. This offers flexibility, scalability, and cost savings compared to traditional hardware-based solutions.
Wrap-Up
In today’s interconnected world, where time is of the essence, NTP servers are indispensable. By meticulously synchronizing clocks across networks, these servers act as the silent guardians of efficiency, security, and seamless operation. Understanding the principles and practices of NTP servers empowers you to build robust and reliable network environments, where every device operates in perfect harmony with time.